What Is MITRE ATT&CK® and How to Use It for Self-Advancement?

Table of contents:
INTRODUCTION
Many blue teams are using MITRE ATT&CK® for advancement in the maturity of their detection and response. Blue team’s arsenal of EDR tools, event logs, and triage tools are all opening up the story of what’s occurring on endpoints. However, anomalies are normal and these alerts and data sources need to be triaged to move forward with response actions or filtering. This MITRE project provides progressing defenders with a knowledge base and resources that can be used as tools to understand attacks and, therefore, the rules and methods for detection. Using ATT&CK for this personal reflection will help you advance in the world of cybersecurity.
REQUIREMENTS
A lab running at least a single Windows 10 or Windows 11 host is critical to any defenders’ personal advancement. Moving forward without practice in a sandboxed lab environment will lead only to a surface-level understanding of ATT&CK techniques. Using a non-sandboxed computer to test adversary techniques is not advised. I highly recommend, at a minimum, increasing the default logging settings (PowerShell, process command line, etc.), installing and configuring Sysmon, and having ProcMon and Wireshark running at all times.
HOW CAN MITRE ATT&CK FRAMEWORK HELP?
First off, let’s look into what ATT&CK stands for. Often referred to by the community as a “framework”, the creators of ATT&CK define it as a “knowledge base”. ATT&CK was created by MITRE to document attacker techniques to be used in adversary emulations. The “CK” in ATT&CK stands for “Common Knowledge”. The tactics and techniques documented in ATT&CK reflect real adversary behaviors. Therefore, each defender should have an awareness of each tactic and technique.
MITRE ATT&CK Tutorial: Before you Begin
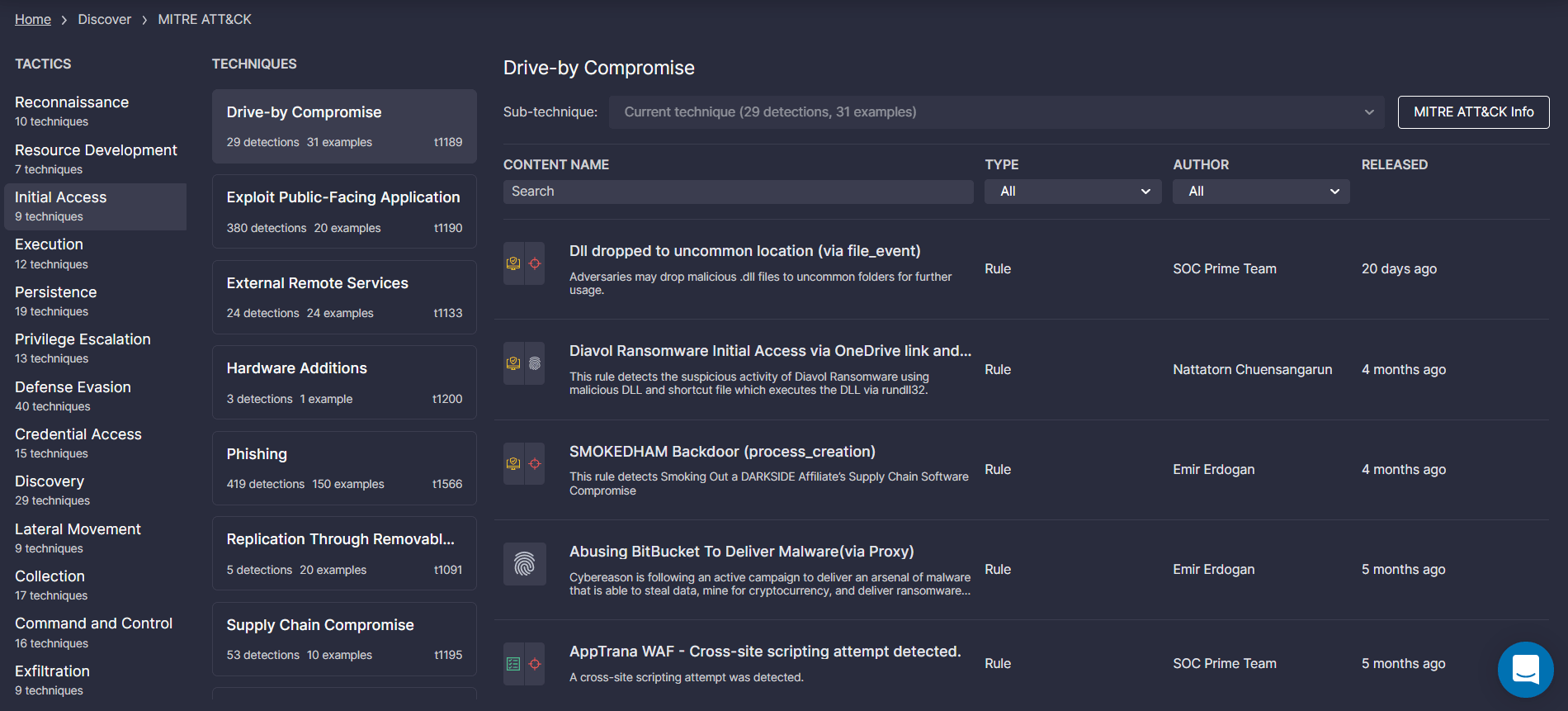
You must identify a place to keep notes on each technique. A simple way to keep notes is via the MITRE ATT&CK Navigator tool, which has the ability to download the matrix to an Excel file. Additionally, SOC Prime’s Detection as Code platform provides a threat-centric selection of detection content aligned with the latest ATT&CK framework with the ability to drill down to tactics, techniques, and related sub-techniques.
MITRE Attack Navigator:
https://mitre-attack.github.io/attack-navigator/enterprise/
ATT&CK resources powered by SOC Prime’s platform:
https://tdm.socprime.com/mitre/
Here are some suggested notes to take:
- Write your own description of the technique.
- Find & keep a copy of PoC (Proof of Concept) code.
- Keep a copy of signatures written or detection ideas.
- Keep a copy (or link) to free & open source tools useful in investigating the technique post-compromise.
- Document the most useful resources you’ve identified for each technique.
- Follow the experts who you found were most influential to your understanding.
HOW TO USE ATT&CK: GENERAL GUIDANCE
1. Identify the ATT&CK Techniques
The fastest and easiest method of using ATT&CK data sources for self progression is to start diving into each technique listed in the ATT&CK matrix from left to right. This brute force approach will get you through each technique; however, it may not be the most efficient to ensure that you’re maturing quickly in areas that matter the most.
Here are some realities of the ATT&CK techniques that should influence how you approach using it to guide learning:
- Some techniques are more difficult to comprehend and act on than others; you don’t want to get overwhelmed by complicated techniques.
- Some techniques are very specific and some are “broad”; I expand on this later.
- Some techniques are more commonly used by adversaries than others. For instance, techniques abusing .NET have become more common as blue teams have better posturing against PowerShell attacks.
Luckily, Travis Smith from Tripwire released a customized ATT&CK framework based on his teaching experience to identify easier methods from more difficult ones. Don’t be afraid to skip and come back to a technique if you find certain techniques harder to comprehend.
For more details, refer to the following resources:
Note: Keep in mind that as ATT&CK evolves, these custom matrices may become outdated.
2. Read the MITRE ATT&CK Technique Page
Each technique listed in ATT&CK is generally more involved than the ~1,000-word summary MITRE provides. For instance, “drive by compromise” listed as the first technique in the top-left of the matrix is a very broad technique. Many methods that fit this technique exist, such as targeting browser extensions, browser bugs, or operating system bugs. The detection and understanding of these methods can differ extremely. For instance, detecting a malicious flash file is different from detecting malicious JavaScript. A flash file exploit is likely contained in the SWF format and probably involves analyzing ActionScript, while a JavaScript-based exploit is a plain text file and likely targets the browser’s JavaScript engine.
The material MITRE provides on each ATT&CK page is a good introduction to the technique. It will generally provide you with the lingo and enough information to guide you in additional research. For many techniques, reading the ATT&CK description will likely leave you with more questions than answers. This is a good thing.
Things to consider
As you read the ATT&CK Technique Page, you should keep the following in mind:
- What terms are vague to me?
For example, what is “ActionScript”?
- How many adversaries are listed as using this technique?
Generally, the more adversaries are listed, the more common and easy to abuse the technique may be.
- How specific is this technique?
Some techniques are very specific that they may not involve as much additional research as a broad technique.
- What offensive tools are listed as being associated with this technique and are they open source or available for testing?
3. Do Some Research
For each technique, there is an abundance of resources located at the bottom of the page. Generally, the resources will cover reporting on adversary implementations of the techniques. The best resources to increase your understanding are those that get into the technical implementation of the techniques and provide links to offensive research or tooling used by adversaries. In addition, be sure to check on any original offensive research report or blog posts on the technique.
Things to consider:
As you read the resources, you should keep the following in mind:
- What nouns are vague to me?
For example, what is “ActionScript”?
- What offensive tools are listed as being associated with this technique and are they open source or available for testing?
- Is there PoC Code available or screenshots of code used to implement the technique?
- What prevention and detection mechanisms are brought forward by the researcher? Do they specifically call out the technique?
- What tools or techniques are available to detect this technique post-compromise?
- Have I covered all aspects of this technique? Are there additional methods of this technique that I haven’t covered?
- Do the authors of this publication have GitHub pages, blog posts, a Twitter account, etc.?
4. Explore Additional Resources (Research)
Since ATT&CK is a common knowledge base, many resources exist from researchers that are not necessarily tied to ATT&CK. The resources may aggregate specific technique examples, identify certain detections, and publish offensive technique research.
Here are a few of my favorite links that cover adversary techniques in ATT&CK, and many include references to additional resources:
- Living of the Land Binaries and Scripts Project at GitHub:
- Sean Metcalf’s Website & Blog
- Roberto Rodriguez’s Threat-Hunter Playbook at GitHub:
- SANS’ Posters
- Casey Smith’s Blog
- Adam Hexacorn’s Blog
Luckily for us, many of these techniques have also been explained by security researchers at conferences over the years. Here are a few classics:
- Defending against PowerShell Attacks – Lee Holmes
- Abusing Windows Management Instrumentation – Matt Graeber
- Designing Active Directory DACL Backdoors – Andy Robbins and Will Schroeder
Things to consider:
See Step 3.
5. Conduct an Emulation (Emulate)
Note: Do not download emulation tools unless you own the network or have explicit permission. Emulation tools are often flagged by Anti-Virus and may contain exploits.
Emulating a technique in a sandboxed lab is great. PoC code provides defenders with a window into mastering the understanding of an attack. Many free emulation scripts and PoC code exist, and these tool sets provide a window into the technique in the form of a boiled-down code. Simply executing the code and watching the result is not enough. An attempt should be made to walk through code line-by-line to understand the technique. In addition, logs captured natively by the operating system, Sysmon, ProcMon should be reviewed. In some instances, capturing additional telemetry with tools such as Wireshark, debuggers, API monitors, memory dumps, etc., may be beneficial. In addition, running forensics tools post emulation (such as those made available by Eric Zimmerman) may be beneficial depending on the technique.
Writing and testing the detection of that technique is another great way to understand the attack and the limitations and context of alerting on that event. Today, many rules are shared via SIGMA, a generic language format for multiple SIEM systems.
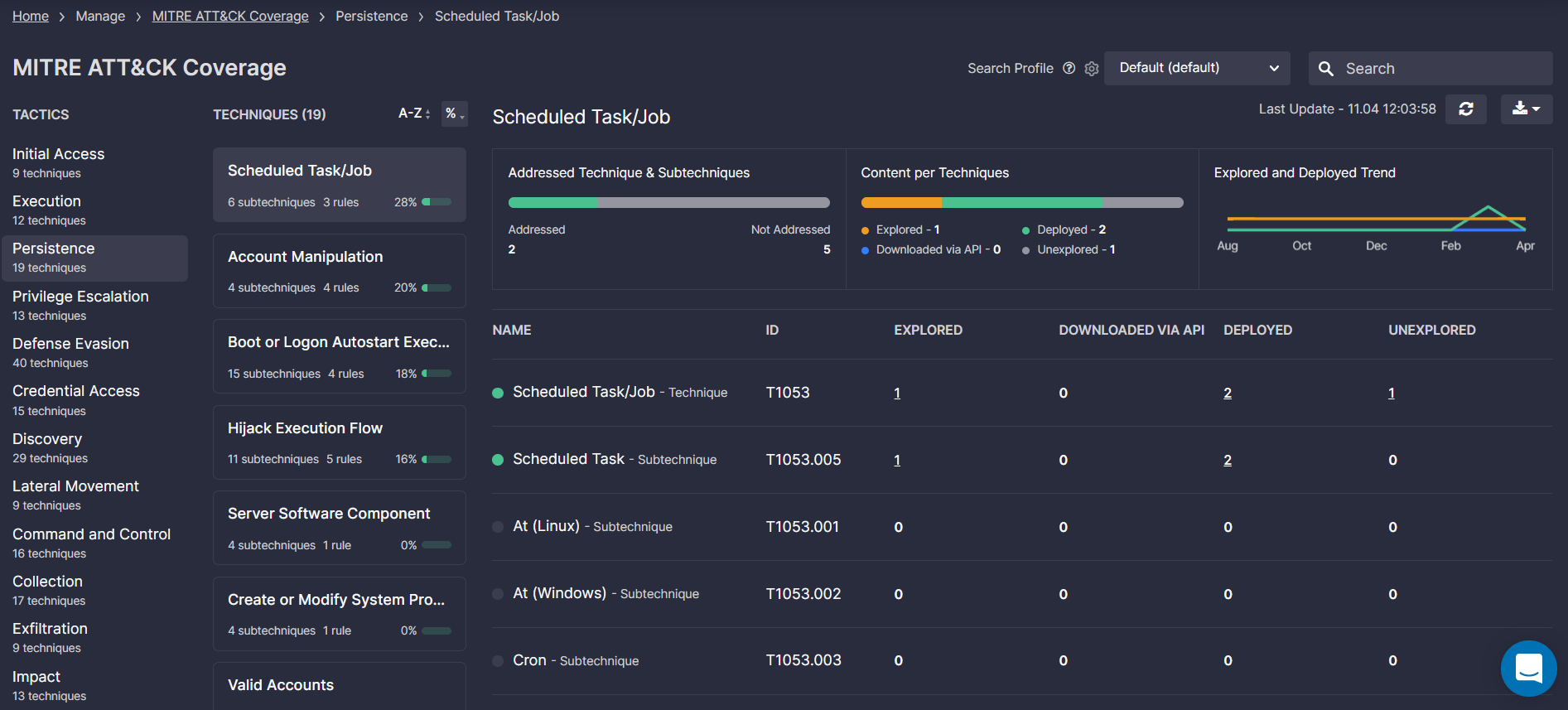
SOC Prime’s Detection as Code platform natively delivers 130,000+ curated Sigma-based detections via subscription to 20+ SIEM and XDR formats which include emulations and rules for most of the techniques available in the latest ATT&CK framework. Create a free account at https://tdm.socprime.com/ and reach the latest detection content tailored to your organization’s threat profile and the security tool in use. With the MITRE ATT&CK Coverage dashboard, you can track the real-time metrics on threat coverage and assess the progress over time on addressed ATT&CK techniques, tactics, and sub-techniques with the content from the SOC Prime’s platform.
Some techniques can be incredibly difficult to understand or replicate without advanced training and experience. It is normal, even after conducting an emulation, gaining insights into the technique, or even writing your own code to not completely understand what is happening. If you’ve made it this far and have lingering questions, reaching out to mentors or researchers directly may be useful.
Things to consider
As you read the resources, you should keep the following in mind:
- Can I change / alter the PoC to bypass detection?
- Are there additional PoCs available that fit in this technique but use a different method?
LIMITATIONS of ATT&CK
Timeliness
The time from discovery or request for a new technique to be published to the technique being published can take several months. Alternatives like following researchers on Twitter is a great way to get ahead of the game. However, separating signal from the noise with the deluge of information that is shared can be a daunting task.
Depth
Not all topics applicable to cybersecurity are covered by ATT&CK techniques. For instance, one is probably not going to learn about the intricacies of use-after-free-based exploits. Looking at other frameworks and knowledge bases such as the MITRE’s Common Weaknesses Enumeration can assist here.
Join SOC Prime’s Detection as Code platform for collaborative cyber defense, threat hunting and discovery to efficiently combat digital threats with the power of a global community of 20,000+ security experts.